QR code
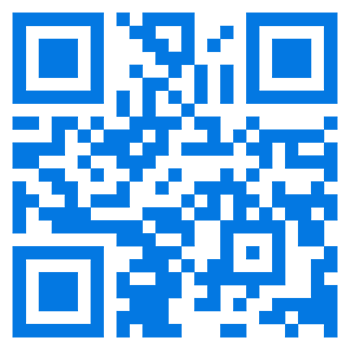
Invented in 1994 and trademarked by Denso Wave, the Quick Response code, or QR code, is a two-dimensional barcode with a larger storage capacity than the standard UPC (Universal Product Code). Its uses include product packaging, advertisements, and labeling products on retail store shelves. QR codes often contain information about a product or a link to a website. For instance, scanning the QR code on this page with your smartphone camera opens the Computer Hope website.
The QR code technology was developed in Japan for use in their automotive industry. Today, it's found in almost every industry and has even been used in currency. In 2011, The Royal Dutch Mint issued the first official coin with a QR code.
What can be encoded on a QR code?
QR Codes can contain any of the following:
- Any plaintext or message. Up to 7,089 numeric characters or 4,296 alphanumeric characters with the 40-L version of the QR code.
- A URL (Uniform Resource Locator) or multiple URLs.
- PDF (Portable Document Format) files.
- Contact information.
- A link to install an app.
- SMS (Short Message Service) messages.
- An e-mail address.
- A telephone number.
- Wi-Fi information.
How can I create a QR code?
There are apps and websites that help you create QR codes. For example, the QR code generator website can be utilized to generate a custom QR code.
How to find what's stored on a QR code
There are websites that help you decode any QR code; our favorite is ZXing, which is also useful for other types of barcodes. Using this service, you can enter a picture URL (Uniform Resource Locator) or upload a picture of a QR code. For example, entering the URL for the QR code shown on this page (https://www.computerhope.com/jargon/q/qr-code.png) displays "https://www.computerhope.com/" as its raw text.
Are QR codes dangerous?
The QR code itself is not dangerous or malicious. However, because anybody can create one, it could point to a questionable website or host malicious JavaScript code. Attacking a device using QR codes is called "attagging," a portmanteau of "attack tagging." The list below contains other ways attagging may target your smartphone.
- Opening a phishing website that looks like where you'd enter payment information for a parking meter.
- Executing malicious JavaScript code that could act as a virus.
- Sending an SMS to a premium text service that charges the phone user.
- Enabling the smartphone's camera, GPS (Global Positioning System), or microphone and stream data from the device to a remote server.
- Reading and transmitting browser history data.
- Stealing sensitive data stored on the smartphone.
How to protect yourself from attagging
You can take the following actions to help prevent yourself from becoming a victim of attagging:
- Learn how to identify phishing attempts and verify the URL the QR code wants to open.
- Examine the QR code and make sure it's not a sticker of a QR code placed over top of another.
- Be cautious of QR codes posted in public.
- When scanning a QR code, use your smartphone's camera instead of a QR code scanning app, as applications can be slower than devices to receive security updates.
- If you're really suspicious of a QR code, take a picture and upload it to a website that deciphers QR code text. See the How to find what's stored on a QR code section above for further information.
App, Barcode, Business terms, Computer acronyms, Hardware terms, Internet terms, Matrix code, Phone terms, Security terms, Semacode, Software terms
